Phishing In Cyber Security. Your company should consider a tiered security approach to lessen the number of phishing attacks and reduce the impact when attacks do occur. When an attack makes it through your security, employees are typically the.

Phishing and the cybersecurity world change on a daily basis, and attacks are becoming increasingly sophisticated.
In a joint advisory issued by fbi in association with cisa of department of homeland security, … Phishing typically refers to scams carried out through email, but very similar scams can be run through text or social media messaging. Instead, organizations must take a layered approach to reduce the number of attacks and lessen their impact when they do occur. Sometimes they try to create a false sense of urgency to get you to respond. The australian cyber security center is warning that fraudsters have recently started sending phishing emails that spoof the agency and contain malware designed to steal banking credentials. But when we talk about phishing, what types of phishing attacks are we specifically talking about? Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. Fake threats from the irs for tax return issues are also. In its 2020 data breach investigations report (dbir), for instance, verizon enterprise found that phishing was the second topmost threat action variety in security incidents and the topmost threat action variety in data breaches. The goal is to trick the email recipient into believing that the message is something they want or need — a. It has been on the list of cyber security trends for a while and won't disappear anytime soon. Phishing attacks continue to play a dominant role in the digital threat landscape. Phishing attacks attempt to gain sensitive, confidential information such as usernames, passwords, credit card information, network credentials, and more. Phishing and fake emails are the biggest security headache for business and amongst the hardest to tackle. No single cybersecurity solution can avert all phishing attacks. Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details, often for malicious reasons, by disguising as a trustworthy entity in an electronic communication. Welcome to cyber security today. Other times they send you an email that seems harmless, and then send you an email. Not all phishing scams work the same way. Protection from phishing attacks is one of the top trends in cyber security. Phishing attacks are just one way that a social engineering attack can be performed, and are designed to take advantage of the human element in cybersecurity. According to the 2019 data breach investigation report by verizon, 32% of all verified data breaches appeared to be phishing. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. Phishing service taken down, phony covid vaccination documents for sale, linux hosting site forced to close and more.
<The best way to combat cyberattacks is to stay informed about the latest attacks. Sometimes they try to create a false sense of urgency to get you to respond. Phishing attacks are just one way that a social engineering attack can be performed, and are designed to take advantage of the human element in cybersecurity. But when we talk about phishing, what types of phishing attacks are we specifically talking about? No single cybersecurity solution can avert all phishing attacks. It works the same like email phishing, except because cyber criminals gain hold of private details using a phone. According to the 2019 data breach investigation report by verizon, 32% of all verified data breaches appeared to be phishing. The australian cyber security center is warning that fraudsters have recently started sending phishing emails that spoof the agency and contain malware designed to steal banking credentials. Phishing service taken down, phony covid vaccination documents for sale, linux hosting site forced to close and more. Fake threats from the irs for tax return issues are also. Phishing typically refers to scams carried out through email, but very similar scams can be run through text or social media messaging. The best way to combat cyberattacks is to stay informed about the latest attacks. This multilayered approach includes employee awareness training. Instead, organizations must take a layered approach to reduce the number of attacks and lessen their impact when they do occur. Protection from phishing attacks is one of the top trends in cyber security. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. A new reality for cybersecurity the chief information security officer (ciso) at a modern enterprise must contend with a myriad of threats. Phishing attacks are widely recognized as the top cause of data. It therefore comes as no surprise that more than a fifth (22%) of data breaches. In a joint advisory issued by fbi in association with cisa of department of homeland security, … Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details, often for malicious reasons, by disguising as a trustworthy entity in an electronic communication. Phishing is a way that cybercriminals steal confidential information, such as online banking logins, credit card details, business login credentials or passwords/passphrases, by sending fraudulent messages (sometimes called 'lures'). Not all phishing scams work the same way. In its 2020 data breach investigations report (dbir), for instance, verizon enterprise found that phishing was the second topmost threat action variety in security incidents and the topmost threat action variety in data breaches. Unsurprisingly, phishing attacks make up a large amount of cyber security incidents. The goal is to trick the email recipient into believing that the message is something they want or need — a. By posing as a legitimate individual or institution via phone or email, cyber attackers use social engineering to manipulate victims into performing specific actions. Phishing and fake emails are the biggest security headache for business and amongst the hardest to tackle. When asked about the best way to thwart cyberattacks, most cybersecurity experts list off a complex list of cutting edge software and hardware solutions meant to keep attackers at bay. Phishing is an internet scam designed to get sensitive information, like your social security number, driver's license, or credit card number. Phishing attacks attempt to gain sensitive, confidential information such as usernames, passwords, credit card information, network credentials, and more. Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. Network security technologies that should be implemented include email and web security, malware protection, user behavior monitoring, and access control. One of the most prevalent types of cybersecurity breaches is phishing.
And that may be the biggest cyber risk of all.
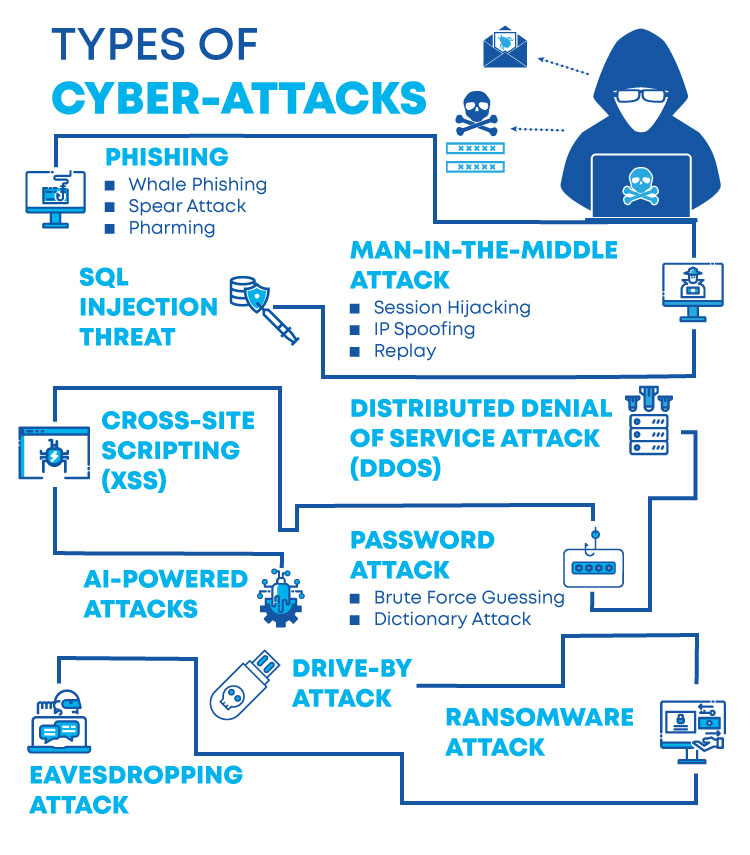
A user may be fooled into clicking a fraudulent link, or misled into entering his or her personal information on a form. Phishing attacks are widely recognized as the top cause of data. A host of new and evolving cybersecurity threats has the information security industry on high alert. Phishing is an internet scam designed to get sensitive information, like your social security number, driver's license, or credit card number. Phishing attacks attempt to gain sensitive, confidential information such as usernames, passwords, credit card information, network credentials, and more. Cybrary's phishing course is an introductory course into phishing attacks and is intended for anyone in the cybersecurity field, including red and blue team members, and end users. Vishing aka 'voice phishing attack' is a new cyber threat that offers cyber criminals the privilege to get money fraudulently. Protection from phishing attacks is one of the top trends in cyber security. No single cybersecurity solution can avert all phishing attacks. Phishing scams are a form of social engineering in which the attacker attempts to trick you into giving them your credentials or access to your system. The australian cyber security center is warning that fraudsters have recently started sending phishing emails that spoof the agency and contain malware designed to steal banking credentials. Unsurprisingly, phishing attacks make up a large amount of cyber security incidents. Network security technologies that should be implemented include email and web security, malware protection, user behavior monitoring, and access control. When asked about the best way to thwart cyberattacks, most cybersecurity experts list off a complex list of cutting edge software and hardware solutions meant to keep attackers at bay.
It works the same like email phishing, except because cyber criminals gain hold of private details using a phone. The goal is to trick the email recipient into believing that the message is something they want or need — a. Dhs s&t's cyber security division director douglas maughan shares how you can protect yourself from a phishing attack. Phishing is a scam that enables a cybercriminal to trick ordinary users into providing personal information, such as login credentials. When an attack makes it through your security, employees are typically the. In a joint advisory issued by fbi in association with cisa of department of homeland security, … The australian cyber security center is warning that fraudsters have recently started sending phishing emails that spoof the agency and contain malware designed to steal banking credentials. Phishing service taken down, phony covid vaccination documents for sale, linux hosting site forced to close and more. Phishing attacks are widely recognized as the top cause of data. According to the 2019 cyber security breaches survey published by the uk government, the. It has been on the list of cyber security trends for a while and won't disappear anytime soon. No single cybersecurity technology can prevent phishing attacks. In its 2020 data breach investigations report (dbir), for instance, verizon enterprise found that phishing was the second topmost threat action variety in security incidents and the topmost threat action variety in data breaches. Fake threats from the irs for tax return issues are also. But when we talk about phishing, what types of phishing attacks are we specifically talking about? When asked about the best way to thwart cyberattacks, most cybersecurity experts list off a complex list of cutting edge software and hardware solutions meant to keep attackers at bay. Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It therefore comes as no surprise that more than a fifth (22%) of data breaches. By posing as a legitimate individual or institution via phone or email, cyber attackers use social engineering to manipulate victims into performing specific actions. These days, phishing isn't limited to emails. Phishing attacks are just one way that a social engineering attack can be performed, and are designed to take advantage of the human element in cybersecurity. Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details, often for malicious reasons, by disguising as a trustworthy entity in an electronic communication. And that may be the biggest cyber risk of all. A user may be fooled into clicking a fraudulent link, or misled into entering his or her personal information on a form.
Instead, organizations must take a layered approach to reduce the number of attacks and lessen their impact when they do occur. No single cybersecurity solution can avert all phishing attacks. This multilayered approach includes employee awareness training. When an attack makes it through your security, employees are typically the. Phishing attacks are just one way that a social engineering attack can be performed, and are designed to take advantage of the human element in cybersecurity. Phishing typically refers to scams carried out through email, but very similar scams can be run through text or social media messaging. It works the same like email phishing, except because cyber criminals gain hold of private details using a phone. Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details, often for malicious reasons, by disguising as a trustworthy entity in an electronic communication. Phishing is a cyber attack that uses disguised email as a weapon. By posing as a legitimate individual or institution via phone or email, cyber attackers use social engineering to manipulate victims into performing specific actions. It therefore comes as no surprise that more than a fifth (22%) of data breaches. The australian cyber security center is warning that fraudsters have recently started sending phishing emails that spoof the agency and contain malware designed to steal banking credentials. Instead, organizations must take a layered approach to reduce the number of attacks and lessen their impact when they do occur. According to the 2019 data breach investigation report by verizon, 32% of all verified data breaches appeared to be phishing. Dhs s&t's cyber security division director douglas maughan shares how you can protect yourself from a phishing attack. Thus, in the united states, phishing scams that use fake fbi warnings for illegal music downloading or watching pornography lead the way. And that may be the biggest cyber risk of all. Protection from phishing attacks is one of the top trends in cyber security. Phishing is a scam that enables a cybercriminal to trick ordinary users into providing personal information, such as login credentials. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. Network security technologies that should be implemented include email and web security, malware protection, user behavior monitoring, and access control. Phishing service taken down, phony covid vaccination documents for sale, linux hosting site forced to close and more. Phishing and fake emails are the biggest security headache for business and amongst the hardest to tackle. Sometimes they try to create a false sense of urgency to get you to respond.